vetKD API
Verifiably encrypted threshold key derivation (vetKD) is a distributed protocol for securely deriving cryptographic keys, referred to as vetKeys. The vetKD API allows canisters to request vetKeys derived using this protocol. Since the key derivation is deterministic, the same inputs will produce the same key, allowing canisters to retrieve keys reliably. Canisters can generate an unlimited number of unique keys by providing different inputs.
Below is a summary of the vetKD API methods and their parameters, described in Candid notation.
// Derives keys based on the provided inputs.
vetkd_derive_key : (record {
// Arbitrary data used to derive keys. This acts as a key identifier - different
// inputs will result in different derived keys. The input does not need to be random.
input : blob;
// A domain separator to ensure that keys are derived within a specific context,
// preventing collisions between different applications or use cases.
context : blob;
// The recipient’s public key, used to encrypt the derived key for secure transport.
transport_public_key : blob;
// The master key from which the derived key is created.
key_id : record { curve : vetkd_curve; name : text };
}) -> (record { encrypted_key : blob; });
// Returns a public key that can be used to verify keys derived using `vetkd_derive_key`.
vetkd_public_key : (record {
// Optional. If provided, the method returns the public key associated with
// the specified `canister_id`. If omitted (`null`), the public key for
// the calling canister is returned.
canister_id : opt canister_id;
// Same as in `vetkd_derive_key`.
context : blob;
// Same as in `vetkd_derive_key`.
key_id : record { curve : vetkd_curve; name : text };
}) -> (record { public_key : blob; });
The full vetKD API specification can be found in the IC interface specification.
Available master keys
The following key names are supported for curve bls12_381_g2:
key_1: Production key available on the ICP mainnet (resides on subnetpzp6eand backed up onuzr34).test_key_1: Test key available on the ICP mainnet (resides on subnetfuqsrand backed up on2fq7c).dfx_test_key: Only available on the local development environment started bydfx.
Note that any canister on the ICP can use any available master key, independent of the subnet on which the canister or the key resides, because the management canister automatically redirects the calls for obtaining vetKeys to the subnet where the master key resides.
Obtaining a vetKey
Deriving a vetKey typically involves both the frontend and backend components of a dapp, as the transport key is usually provided by the user.
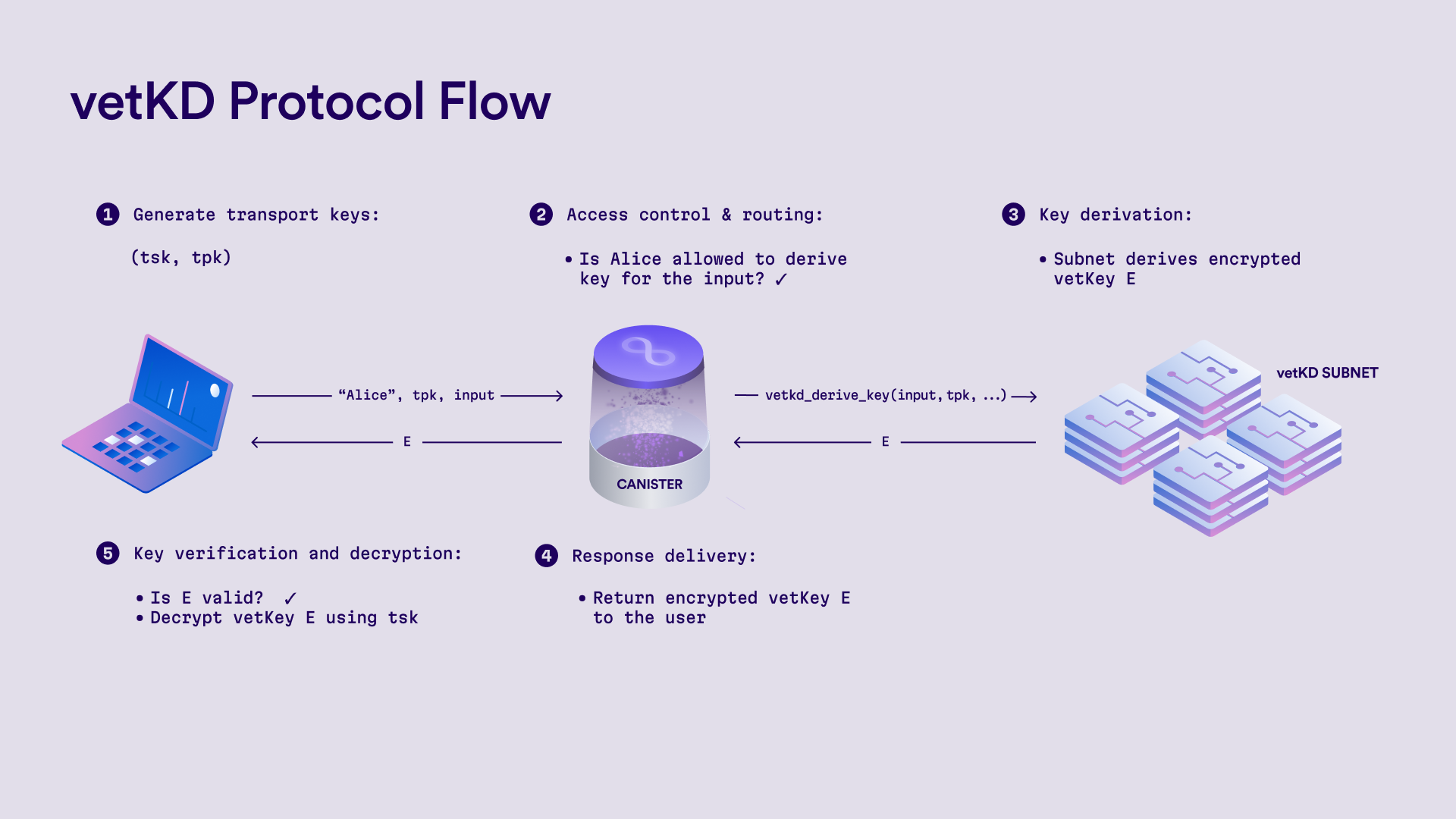
Step 1: Implement canister endpoints
Expose the vetKD endpoints in the backend canister API so that the frontend can retrieve and verify vetKeys.
In this example, an encoding of the caller's identity is used as part of the context parameter to VetKDDeriveKeyArgs.
Since the dapp uses the caller's identity for derivation, the dapp is sure that
the vetKey returned is both unique to that caller and input, and that caller is the only party which can retrieve that
particular key.
Using the caller-provided input parameter, the caller can derive arbitrarily many unique vetKeys that only that user can retrieve and decrypt.
- Motoko
- Rust
import Array "mo:base/Array";
import Blob "mo:base/Blob";
import ManagementCanister "mo:ic-vetkeys/ManagementCanister";
import Nat8 "mo:base/Nat8";
import Principal "mo:base/Principal";
import Text "mo:base/Text";
actor class () {
let DOMAIN_SEPARATOR = Blob.toArray(Text.encodeUtf8("example-vetkd-dapp"));
/// Derive encrypted vetKey for caller's principal.
public shared ({caller}) func vetkd_derive_key(transportKey : Blob, input : Blob) : async Blob {
await ManagementCanister.vetKdDeriveKey(input, context(caller), testKeyId(), transportKey)
};
public shared ({caller}) func publicKey() : async Blob {
await ManagementCanister.vetKdPublicKey(null, context(caller), testKeyId())
};
private func testKeyId() : ManagementCanister.VetKdKeyid {
{curve = #bls12_381_g2; name = "test_key_1"}
};
private func context(principal : Principal) : Blob {
let principalBytes = Blob.toArray(Principal.toBlob(principal));
let flattened = Array.flatten([[Nat8.fromNat(DOMAIN_SEPARATOR.size())], DOMAIN_SEPARATOR, principalBytes]);
Blob.fromArray(flattened);
}
}
use candid::Principal;
use ic_cdk::management_canister::{VetKDCurve, VetKDDeriveKeyArgs, VetKDKeyId, VetKDPublicKeyArgs};
use ic_cdk::update;
const DOMAIN_SEPARATOR: &[u8] = b"example-vetkd-dapp".as_slice();
/// Derive encrypted vetKey for caller's principal.
#[update]
async fn vetkd_derive_key(transport_public_key: Vec<u8>, input: Vec<u8>) -> Vec<u8> {
let caller = ic_cdk::api::msg_caller();
let request = VetKDDeriveKeyArgs {
input,
context: context(caller),
transport_public_key,
key_id: bls12_381_g2_test_key(),
};
let reply = ic_cdk::management_canister::vetkd_derive_key(&request)
.await
.expect("failed to derive key");
reply.encrypted_key
}
#[update]
async fn vetkd_public_key() -> Vec<u8> {
let caller = ic_cdk::api::msg_caller();
let request = VetKDPublicKeyArgs {
canister_id: None,
context: context(caller),
key_id: bls12_381_g2_test_key(),
};
let reply = ic_cdk::management_canister::vetkd_public_key(&request)
.await
.expect("failed to derive key");
reply.public_key
}
fn bls12_381_g2_test_key() -> VetKDKeyId {
VetKDKeyId {
curve: VetKDCurve::Bls12_381_G2,
name: "test_key_1".to_string(),
}
}
fn context(principal: Principal) -> Vec<u8> {
[DOMAIN_SEPARATOR.len() as u8]
.into_iter()
.chain(DOMAIN_SEPARATOR.to_vec().into_iter())
.chain(principal.as_slice().to_vec().into_iter())
.collect()
}
// Export the interface for the smart contract.
ic_cdk::export_candid!();
Step 2: Generate a transport key pair and pass the transport public key to the canister
In this step, the frontend generates a transport private key and passes the corresponding transport public key to the canister in order to obtain the encrypted vetKeys that can only be decrypted by the frontend.
- Typescript
import { DerivedPublicKey, TransportSecretKey, EncryptedVetKey } from "@dfinity/vetkeys";
const transportSecretKey = TransportSecretKey.random();
const canisterClient = // get canister client, usually auto-generated code from canister's candid interface
// unique `input` should be provided for each derived vetKey
// we only need one vetKey in this example, so we choose to have the simplest possible `input` - an empty vector
const input = new Uint8Array(0);
// the called canister uses the caller's principal as part of `context` when calling the management canisters `vetkd_derive_key` endpoint under the hood (see code in Step 1)
const encryptedVetKeyBytes = await canisterClient.vetkd_derive_key(transportSecretKey.publicKeyBytes(), input);
const encryptedVetKey = EncryptedVetKey(encryptedVetKeyBytes);
Step 3: Retrieve the vetKD public key from the backend canister
Once retrieved, you must decrypt and verify the received encrypted vetKey.
- Typescript
// the called canister uses the caller's principal as part of `context` when calling the management canisters `vetkd_public_key` endpoint under the hood (see code in Step 1)
const publicKeyBytes = await canisterClient.vetkd_public_key();
const publicKey = DerivedPublicKey.deserialize(publicKeyBytes);
// pass `input` from Step 2 to the verification function
const vetKey = encryptedVetKey.decryptAndVerify(transportSecretKey, publicKey, input);
API fees
The fees for the vetKD APIs are defined below. The threshold vetKD test key resides on the 13-node application subnet fuqsr, while the threshold vetKD production key resides on the 34-node-sized fiduciary subnet pzp6e. The subnet size where the vetKD key resides and the vetKeys are computed defines the resulting cost. The size of the subnet of the calling canister does not matter for the fees. For costs in USD, the USD/XDR exchange rate as of May 22, 2025, has been used.
If a canister using this feature is intended to be blackholed or used by other canisters, it's recommended to send more cycles with each call than the currently advertised cost. This ensures that, if the subnet's size increases in the future (leading to higher signature costs), the call will still succeed. Any unused cycles are automatically refunded.
Fees for deriving one vetKey using the vetkd_derive_key API of the management canister:
| Key type (key name) | Cycles | USD | Signing subnet (size) |
|---|---|---|---|
Production key (key_1) | 26_153_846_153 | $0.0354325 | pzp6e (34) |
Test key (test_key_1) | 10_000_000_000 | $0.0135482 | fuqsr (13) |
Offline Key Derivation
As an alternative to using vetkd_public_key to perform key derivation, it is also possible to perform the key derivation
completely offline, avoiding network cost.
These example snippets demonstrate using the vetkeys utility libraries to perform the derivation for
key_1, with a canister "urq22-tyaaa-aaaag-audia-cai", and a context string of "context-string".
- Rust
- Typescript
let key_id = VetKDKeyId {
curve: VetKDCurve::Bls12_381_G2,
name: "key_1".to_string(),
};
let key1 = MasterPublicKey::for_mainnet_key(&key_id)?;
let canister_id = candid::Principal::from_text("urq22-tyaaa-aaaag-audia-cai")?;
let canister_key = key1.derive_canister_key(canister_id.as_slice());
let derived_key = canister_key.derive_sub_key(b"context-string");
const masterKey = MasterPublicKey.productionKey();
const canisterId = hexToBytes("0000000000c0a0d00101"); // the byte encoding of the canister identifier
const canisterKey = masterKey.deriveCanisterKey(canisterId);
const derivedKey = canisterKey.deriveSubKey(new TextEncoder().encode("context-string"));
Master Public Keys
The value of the master public keys used in the production network are:
key_1:a9caf9ae8af0c7c7272f8a122133e2e0c7c0899b75e502bda9e109ca8193ded3ef042ed96db1125e1bdaad77d8cc60d917e122fe2501c45b96274f43705edf0cfd455bc66c3c060faa2fcd15486e76351edf91fecb993797273bbc8beaa47404test_key_1:ad86e8ff845912f022a0838a502d763fdea547c9948f8cb20ea7738dd52c1c38dcb4c6ca9ac29f9ac690fc5ad7681cb41922b8dffbd65d94bff141f5fb5b6624eccc03bf850f222052df888cf9b1e47203556d7522271cbb879b2ef4b8c2bfb1
These can be loaded using the VetKD utility libraries as follows:
- Rust
- Typescript
let key1_bytes = "a9caf...";
let key1 = MasterPublicKey::deserialize(hex::decode(key_1)?)?;
let key1_bytes = "a9caf...";
let key1 = MasterPublicKey.deserialize(Uint8Array.fromHex(key1_bytes));
Using the MasterPublicKey is is possible to perform offline key
derivation as described above in the section "Offline Key Derivation".
PocketIC Test Keys
PocketIC contains hardcoded keys for testing purposes, which are:
key_1: 8c800b5cff00463d26e8167369168827f1e48f4d8d60f71dd6a295580f65275b5f5f8e6a792c876b2c72492136530d0710a27522ee63977a76216c3cef9e70bfcb45b88736fc62142e7e0737848ce06cbb1f45a4a6a349b142ae5cf7853561e0
test_key_1: 9069b82c7aae418cef27678291e7f2cb1a008a500eceba7199bffca12421b07c158987c6a22618af3d1958738b2835691028801f7663d311799733286c557c8979184bb62cb559a4d582fca7d2e48b860f08ed6641aef66a059ec891889a6218
dfx_test_key: b181c14cf9d04ba45d782c0067a44b0aaa9fc2acf94f1a875f0dae801af4f80339a7e6bf8b09fcf993824c8df3080b3f1409b688ca08cbd44d2cb28db9899f4aa3b5f06b9174240448e10be2f01f9f80079ea5431ce2d11d1c8d1c775333315f